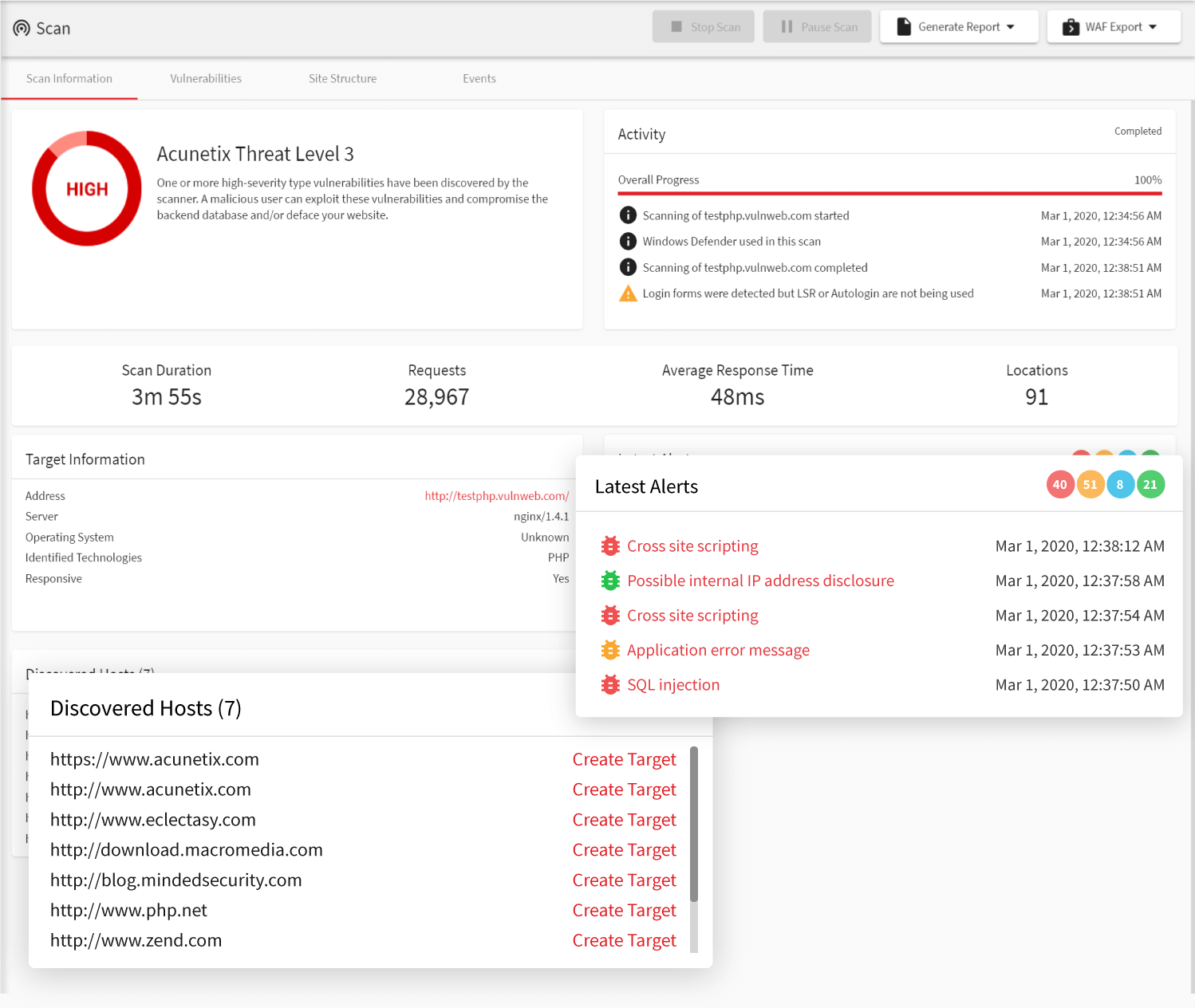
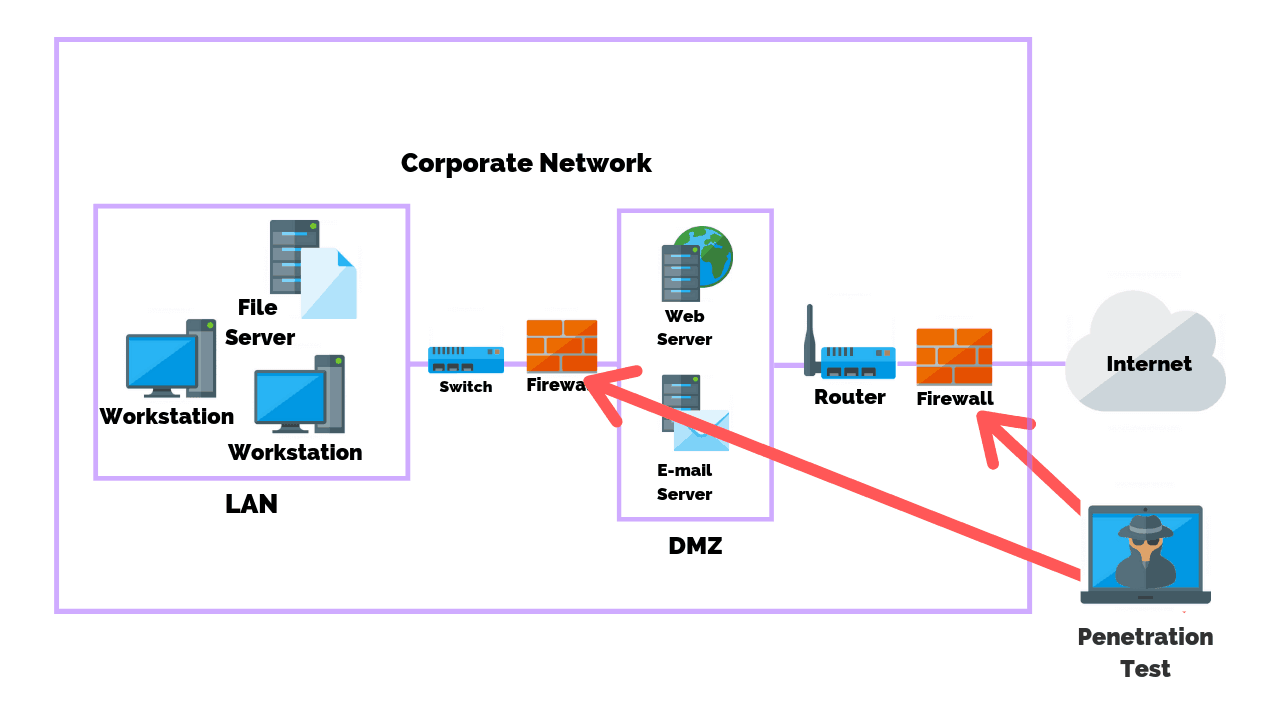
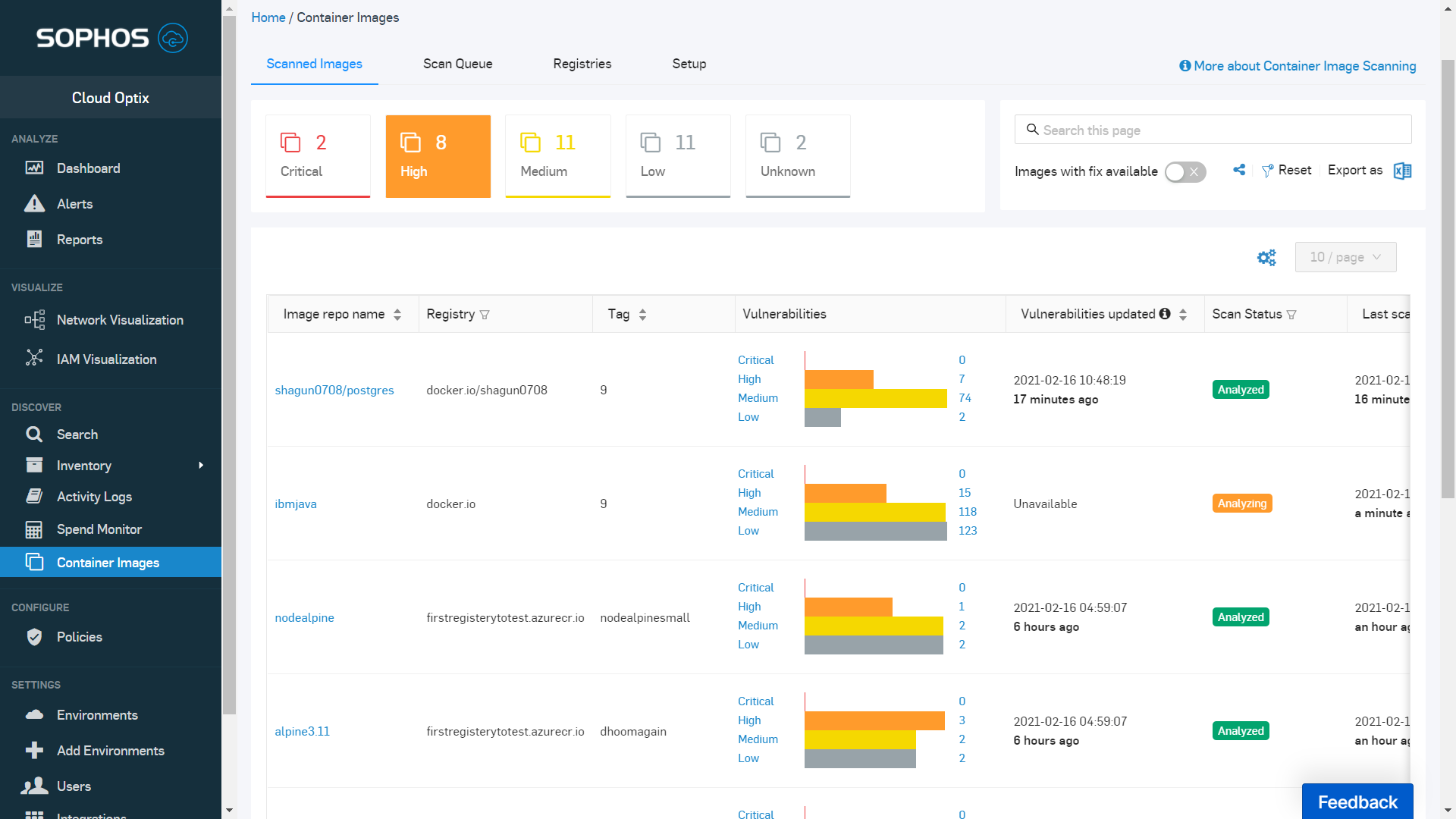
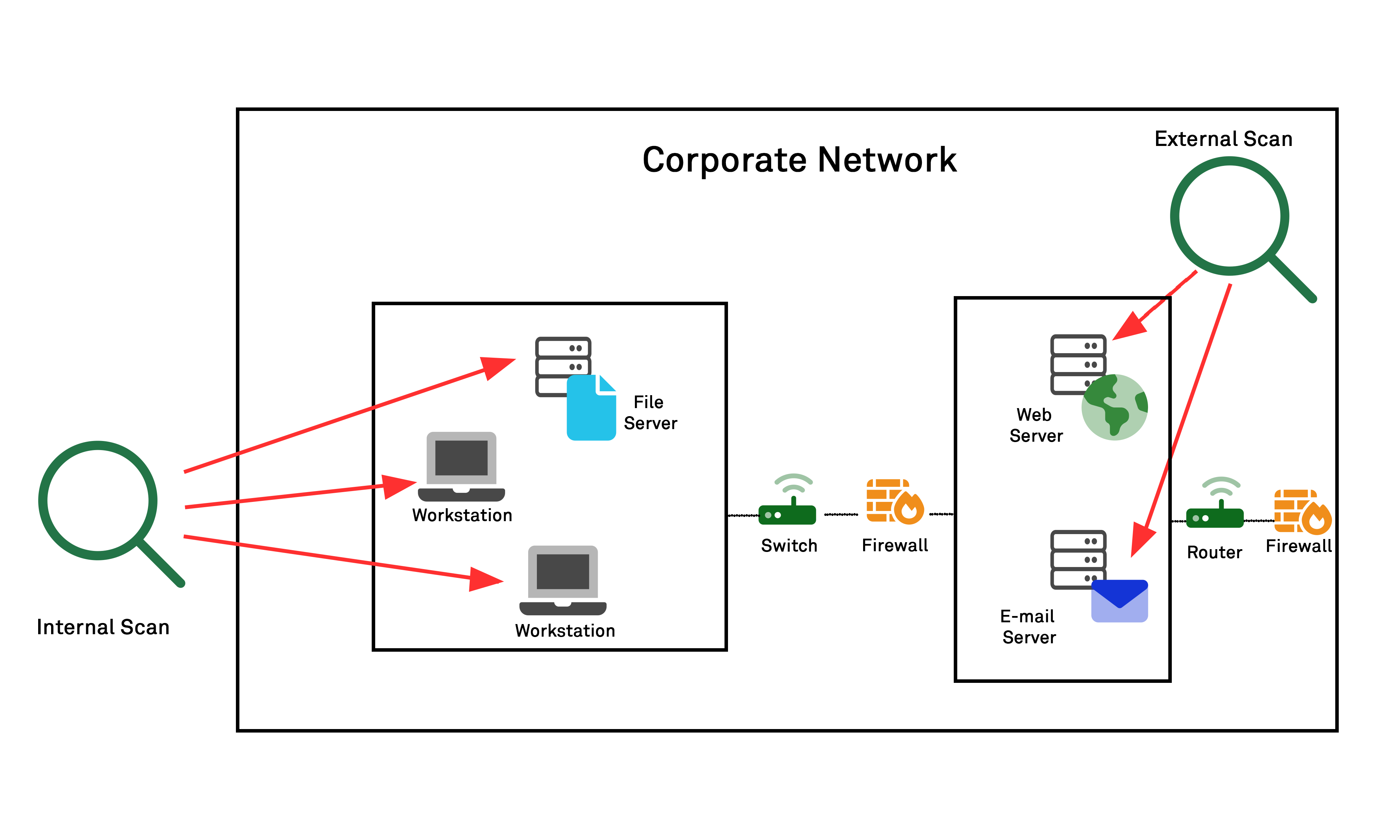
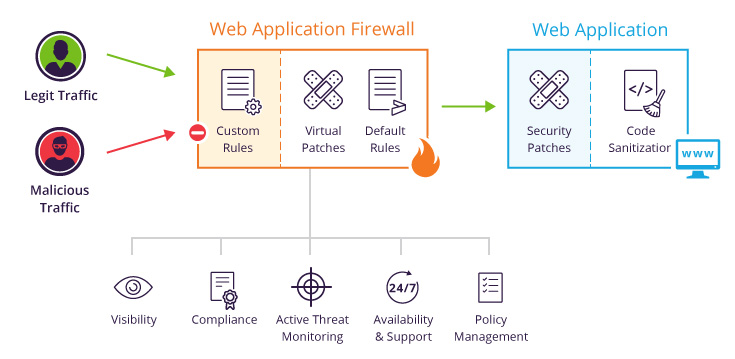
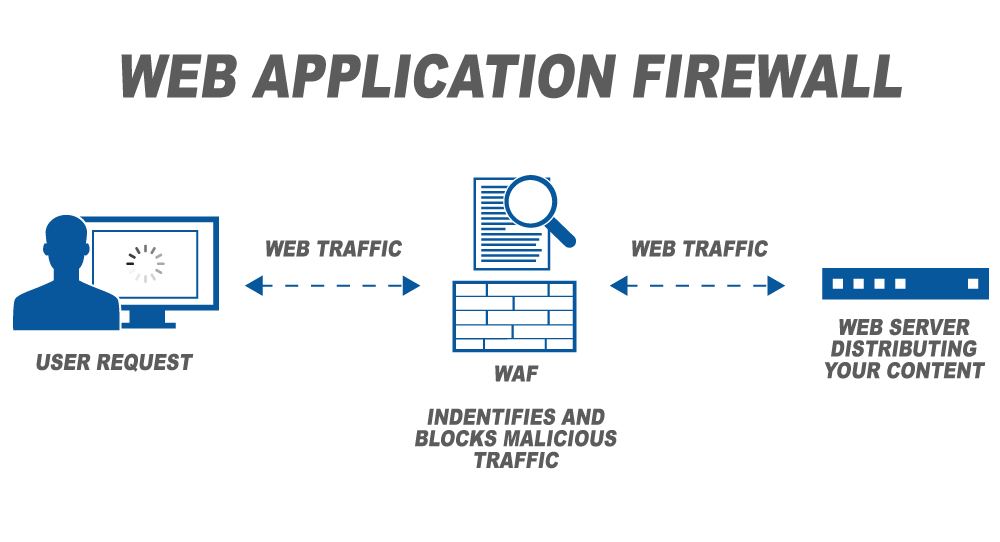
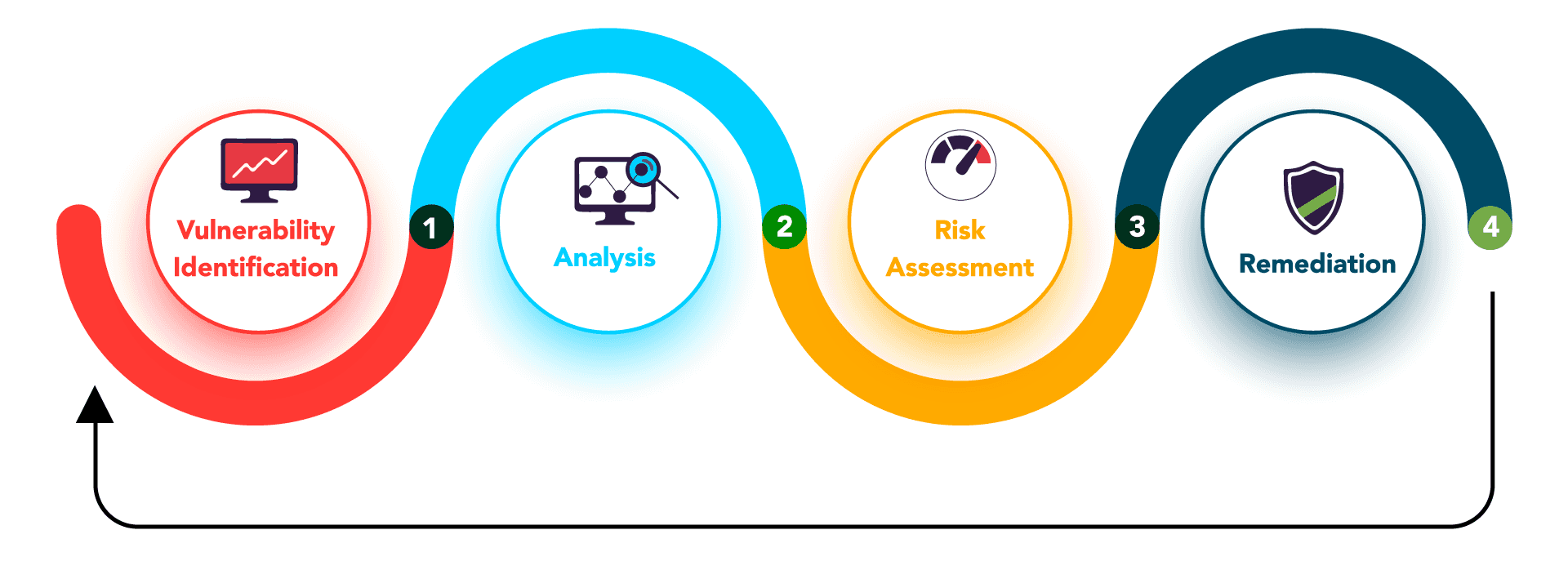
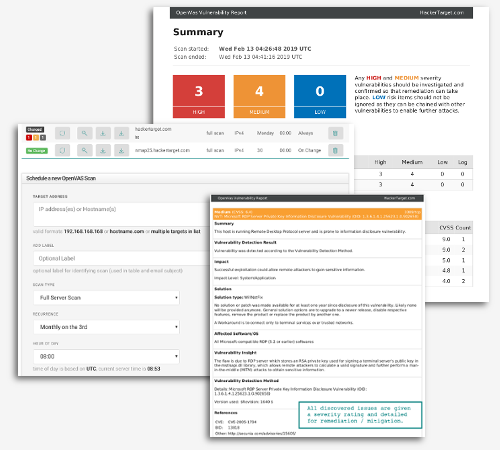
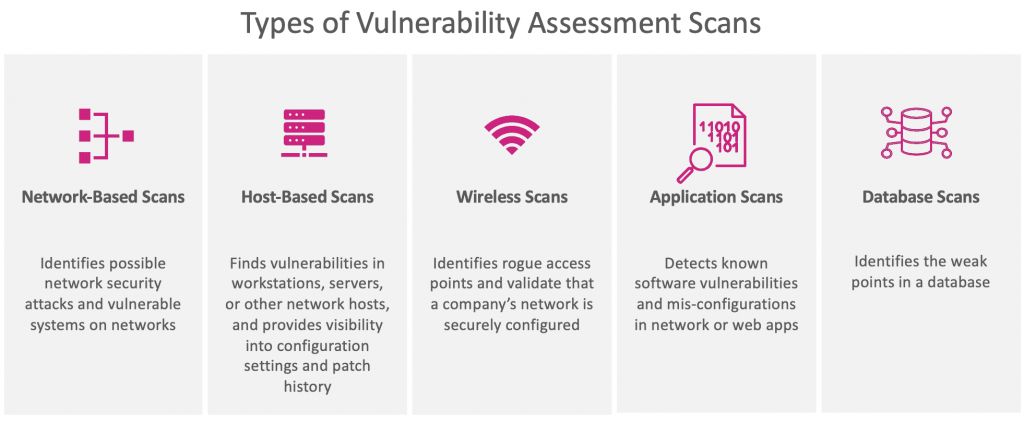
How to Configure NetScaler Application Firewall Signatures Protection Based on Vulnerability Scan Result of QualysGuard

How to Configure NetScaler Application Firewall Signatures Protection Based on Vulnerability Scan Result of QualysGuard